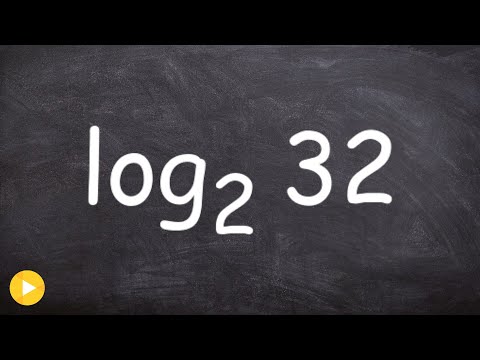Evaluate log base 2 of 256 | Mathway
great www.mathway.com
Evaluate log base 2 of 256. log2 (256) log 2 ( 256) Rewrite as an equation. log2(256) = x log 2 ( 256) = x. Rewrite log2 (256) = x log 2 ( 256) = x in exponential form using the definition of a logarithm. If x x and b b are positive real numbers and b b does not equal 1 1, then logb (x) = y log b ( x) = y is equivalent to by = x b y = x.
79 People Used
More Info ››
Log base 2 of 256 converter | Evaluate Log2 256 Online
new www.coolmathgames9.com
log base 2 of 256 converter calculator for mathematics logarithm bases. Learn logarithm formula and equation using online tool and how to evaluate Log2 256Multiplication‧Log Base Converter Online
197 People Used
More Info ››
Video result for Evaluate Log2 256
Log2(256) or Log Base 2 of 256? - getcalc.com
top getcalc.com
The below is the work with steps to find what is log base 2 of 256 shows how the input values are being used in the log base 2 functions. Formula: log b (x) = y, if b y = x. Input: x = 256. b = 2. Solution: y = log 2 256. = log 2 2 8.
468 People Used
More Info ››
SOLUTION: log2 256=x Find the value of x
top www.algebra.com
Answers. Click here to see ALL problems on Exponential-and-logarithmic-functions. Question 545825: log2 256=x. Find the value of x. Answer by vleith (2983) ( Show Source ): You can put this solution on YOUR website! log2 256=x is the same as asking. I bet you can tell what x is there.
119 People Used
More Info ››
Evaluate. log (down)2 256 . Write a conclusion statement.
new e-eduanswers.com
log 256 can most easily be found by rewriting 256 as a power of 2: 2. 2^5 * 2^3 = 32*8 = 256, so 2^ (5 + 3) = 2^8. Then we have: log 256. 2 2 = 256. Alternatively, write: log (down)2 256 = log (down)2 2^8 = 2*8 = 256. Note that your "log (down)^2 and the function y = 2^x are inverse functions that effectively cancel one another.
383 People Used
More Info ››
Evaluate Log2 (log4 256) - MCQ's Mentor
best www.mcqsmentor.com
Main Menu. Computer Menu Toggle. Computer Science
306 People Used
More Info ››
Evaluate log base 4 of 256 | Mathway
best www.mathway.com
Evaluate log base 4 of 256. log4 (256) log 4 ( 256) Rewrite as an equation. log4(256) = x log 4 ( 256) = x. Rewrite log4 (256) = x log 4 ( 256) = x in exponential form using the definition of a logarithm. If x x and b b are positive real numbers and b b does not equal 1 1, then logb (x) = y log b ( x) = y is equivalent to by = x b y = x. 4x ...
370 People Used
More Info ››
Log base 2 Calculator Log2
new www.logcalculator.net
Log base 2 calculator finds the log function result in base two. Calculate the log2(x) logarithm of a real number, find log base 2 of a number.
143 People Used
More Info ››
Logarithm Calculator log(x)
best www.logcalculator.net
The logarithm log b (x) = y is read as log base b of x is equals to y. Please note that the base of log number b must be greater than 0 and must not be equal to 1. And the number (x) which we are calculating log base of (b) must be a positive real number. For example log 2 of 8 is equal to 3.
362 People Used
More Info ››
Log Calculator
hot www.calculator.net
This free log calculator solves for the unknown portions of a logarithmic expression using base e, 2, 10, or any other desired base. Learn more about log rules, or explore hundreds of other calculators addressing topics such as math, finance, health, and fitness, among others.
459 People Used
More Info ››
Logarithmic Equation Calculator - Symbolab
new www.symbolab.com
Identities Proving Identities Trig Equations Trig Inequalities Evaluate Functions Simplify. Statistics. ... \log _2(x^2-6x)=3+\log _2(1-x) logarithmic-equation-calculator. en. Related Symbolab blog posts. High School Math Solutions - Exponential Equation Calculator.
212 People Used
More Info ››
SOLUTION: How do i evaluate the following: log3 81 log4 ...
great www.algebra.com
Question 93116: How do i evaluate the following: log3 81 log4 256 log2 (1/32) log5 1 log3 (-1) Please help thanks Lucy Found 2 solutions by stanbon, venugopalramana:
242 People Used
More Info ››
Log (Logarithm) Calculator - Calculate Logarithm
best miniwebtool.com
The Log (Logarithm) Calculator is used to calculate the logarithm log b x for a base b and a number x. Logarithm. The logarithm of a number x with respect to base b is the exponent to which b has to be raised to yield x. In other words, the logarithm of y to base b is the solution y of the following equation:
131 People Used
More Info ››
How do you evaluate log_7 (1/49)? | Socratic
top socratic.org
log_7(1/49)=x 7^x=(1/49) 11945 views around the world You can reuse this answer Creative Commons License
275 People Used
More Info ››
Solve log_{4}({256})+log_{x}({16})=6 | Microsoft Math Solver
hot mathsolver.microsoft.com
Solve your math problems using our free math solver with step-by-step solutions. Our math solver supports basic math, pre-algebra, algebra, trigonometry, calculus and more.
457 People Used
More Info ››
Solving Log Equations with Exponentials | Purplemath
best www.purplemath.com
log 2 ( x2 - 2 x) = 3. Now the equation is arranged in a useful way. At this point, I can use The Relationship to convert the log form of the equation to the corresponding exponential form, and then I can solve the result: log 2 ( x2 - 2 x) = 3. 2 3 = x2 - 2 x. 8 = x2 - 2 x. 0 = x2 - 2 x - 8. 0 = ( x - 4) ( x + 2)
280 People Used
More Info ››
Logarithm Calculator | log(x) Calculator
best www.rapidtables.com
Anti-logarithm calculator. In order to calculate log-1 (y) on the calculator, enter the base b (10 is the default value, enter e for e constant), enter the logarithm value y and press the = or calculate button: = Calculate × Reset
345 People Used
More Info ››
[Solved] Evaluate the following expression. you should do ...
best brainly.com
Evaluate the following expression. you should do this without a calculator log4 256 - 12866950
392 People Used
More Info ››
Solved: For evaluate the logarithms.a. log4 256 − log4 16b ...
hot www.chegg.com
Answer to For evaluate the logarithms.a. log4 256 − log4 16b. .
137 People Used
More Info ››
Solve log_{4}({256}) | Microsoft Math Solver
new mathsolver.microsoft.com
Solve your math problems using our free math solver with step-by-step solutions. Our math solver supports basic math, pre-algebra, algebra, trigonometry, calculus and more.
193 People Used
More Info ››
Popular Searching
Useful Blogs
How to fix Server Login Issues?
Find out If Someone Else is Logging in Your Facebook Account
10 Straightforward Ways to Stay Safe from Cyber Attacks
User Authentication: Understanding The Basics & Top Tips
Video result
Related News
We found a lot of relevant information for Evaluate Log2 256. We provide the official link and a number of helpful pages for the login above. They are reliable sites collected by LoginNote. Please check it thoroughly!
How do you collect the data for Evaluate Log2 256?
We prioritize finding the official login links for all searches. Besides that, relevant information such login instructions, requirements, and accounts may be also given.
Will you provide the correct login pages?
Yes. On most of the results recommended for Evaluate Log2 256, we provide the official links, they tend to be on the top of the page. Please check it.
If I can not login into a page, could you help me?
Firstly, you need to recheck what personal information you offer to confirm the login information is valid or not. Secondly, it is possible that the official page is temporarily suspended, so you can only wait. Or it is also possible that the links directing to the login pages are in some trouble, then you can contact us via email, we will overcome it right away.
Where can I find the official link for Evaluate Log2 256?
At each result for searches, we also enclose a link heading to the official login portal. It is often on the top of the recommendation page. The official link for Evaluate Log2 256 is the same.