See Further Detailed Guides Of The Login Process at discord.boats
By clicking discord.boats, users can detect more useful information for their login.
Visit site: discord.boats
MEE6 | Discord Boats
tip discord.boats
MEE6 is a fun, feature packed, and fantastic Discord bot that aims to connect people to the communities they love on Discord, that is currently in over 3.4 Million servers across the platform. Discord Boats is a growing directory of Discord bots to enhance your server - Find the perfect bot for your needs and add it to your server easily ...
406 People Used
Login | Discord Boats | A list of Discord bots
trend discord.boats
Discord Boats is a growing directory of Discord bots to enhance your server - Find the perfect bot for your needs and add it to your server easily, quickly and for free. Your AdBlock is on We know ads can be annoying, but they're what allow us to make all of Discord Boats available for free.
460 People Used
Login | Discord Boats | A list of Discord bots
new discord.boats
Discord Boats is a growing directory of Discord bots to enhance your server - Find the perfect bot for your needs and add it to your server easily, quickly and for free. Your AdBlock is on We know ads can be annoying, but they're what allow us to make all of Discord Boats available for free.
316 People Used
Login | Discord Boats | A list of Discord bots
trend discord.boats
Discord Boats is a growing directory of Discord bots to enhance your server - Find the perfect bot for your needs and add it to your server easily, quickly and for free. Your AdBlock is on We know ads can be annoying, but they're what allow us to make all of Discord Boats available for free.
166 People Used
Login | Discord Boats | A list of Discord bots
new discord.boats
Discord Boats is a growing directory of Discord bots to enhance your server - Find the perfect bot for your needs and add it to your server easily, quickly and for free. Your AdBlock is on We know ads can be annoying, but they're what allow us to make all of Discord Boats available for free.
449 People Used
Login | Discord Boats | A list of Discord bots
best discord.boats
Discord Boats is a growing directory of Discord bots to enhance your server - Find the perfect bot for your needs and add it to your server easily, quickly and for free. Your AdBlock is on We know ads can be annoying, but they're what allow us to make all of Discord Boats available for free.
215 People Used
Login | Discord Boats | A list of Discord bots
trend discord.boats
Discord Boats is a growing directory of Discord bots to enhance your server - Find the perfect bot for your needs and add it to your server easily, quickly and for free. Your AdBlock is on We know ads can be annoying, but they're what allow us to make all of Discord Boats available for free.
198 People Used
Login | Discord Boats | A list of Discord bots
trend discord.boats
Discord Boats is a growing directory of Discord bots to enhance your server - Find the perfect bot for your needs and add it to your server easily, quickly and for free. Your AdBlock is on We know ads can be annoying, but they're what allow us to make all of Discord Boats available for free.
361 People Used
Bots | Discord Boats | A list of Discord bots
great discord.boats
Your AdBlock is on. We know ads can be annoying, but they're what allow us to make all of Discord Boats available for free. Please help us continue to provide you with our service for free by whitelisting Discord.Boats on your ad blocker. if you really can't stand to see another ad again, then please consider support our work with a contribution to Discord.Boats and get some cool perks along ...
402 People Used
Botzilla | Discord Boats
great discord.boats
Member Counter Bot. A counting bot that counts members, users, bots with the help of voice channels. Easy Setup Only one command is needed for the setup of bot, m-setup. Fast Response and No Downtime With the help of fastest system we give faster response for every command and we keep our eyes on bot for no downtime issue.
492 People Used
Wiki-Bot | Discord Boats
trend discord.boats
Wiki-Bot. Wiki-Bot is a bot for Discord with the purpose to easily link and search MediaWiki sites like Gamepedia and Fandom wikis. Wiki-Bot shows short descriptions and additional info about pages and is able to resolve redirects and follow interwiki links.. Wiki-Bot has translations for English, German, French, Dutch, Polish, Portuguese, Russian, Turkish and Chinese.
114 People Used
Anti N-Word Bot | Discord Boats
hot discord.boats
Shows a list of everyone who has an N--word pass. Discord Boats is a growing directory of Discord bots to enhance your server - Find the perfect bot for your needs and add it to your server easily, quickly and for free.
362 People Used
Transformer | Discord Boats
hot discord.boats
Your AdBlock is on. We know ads can be annoying, but they're what allow us to make all of Discord Boats available for free. Please help us continue to provide you with our service for free by whitelisting Discord.Boats on your ad blocker. if you really can't stand to see another ad again, then please consider support our work with a contribution to Discord.Boats and get some cool perks along ...
122 People Used
User Info | Discord Boats
trend discord.boats
This bot displays roblox information about any discord user you tag. It searches through RoWifi, Bloxlink, and RoVer/Eryn to find their roblox ID and then displays a summary of their roblox profile along with a link. The bot automatically has administrator permissions, simply so that it can see and talk in every channel.
479 People Used
Login | Discord Boats | A list of Discord bots
great discord.boats
Discord Boats is a growing directory of Discord bots to enhance your server - Find the perfect bot for your needs and add it to your server easily, quickly and for free. ... Login with Discord . Join more than half a million registered users!
225 People Used
DLookup | Discord Boats
best discord.boats
Discord Lookup! Discord Lookup allows you to check the information of any discord user, you can see their Badges, Creation date, Name, Profile picture and more! How to use it : To search for a user use the "!lookup" command together with the user ID. How to extract the id of some user? To extract the id of a user follow this tutorial made by ...
126 People Used
User Info | Discord Boats
trend discord.boats
Discord to Roblox User Information Bot. This bot displays roblox information about any discord user you tag. It searches through RoWifi, Bloxlink, and RoVer/Eryn to find their roblox ID and then displays a summary of their roblox profile along with a link. The bot automatically has administrator permissions, simply so that it can see and talk ...
335 People Used
Login | Discord Boats | A list of Discord bots
great discord.boats
Discord Boats is a growing directory of Discord bots to enhance your server - Find the perfect bot for your needs and add it to your server easily, quickly and for free. ... Login with Discord . Join more than half a million registered users! Login Join Discord Guild. After clicking the login button you will be redirected to discord.com.
224 People Used
Logger | Discord Boats
new discord.boats
Logger is a no bs logging bot supporting maximum customization & user control. Logger is a no bs logging bot supporting maximum customization & user control. × Your AdBlock is on. We know ads can be annoying, but they're what allow us to make all of Discord Boats available for free.
457 People Used
Login | Discord Boats | A list of Discord bots
hot discord.boats
Discord Boats is a growing directory of Discord bots to enhance your server - Find the perfect bot for your needs and add it to your server easily, quickly and for free. ... Login with Discord . Join more than half a million registered users! Login Join Discord Guild. After clicking the login button you will be redirected to discord.com.
301 People Used
Popular Searching
Saving Tips

Can't Log in to Tiktok: Here are The Best Solutions Ever for You

What Is Data Breach? How Can User Detect a Data Breach to Report?
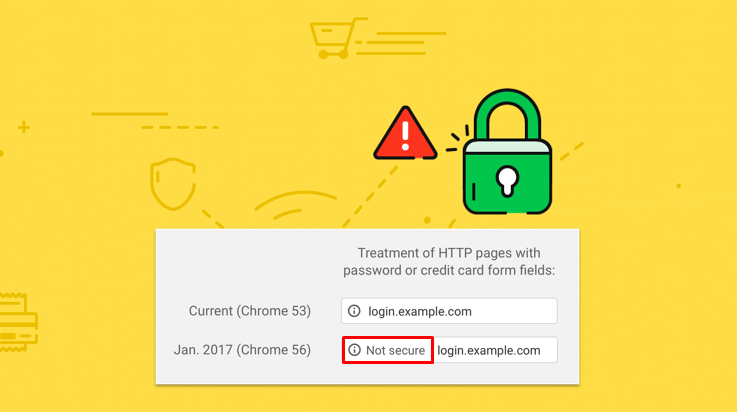
Things to Know When Entering Your Account to "Not Secure" Website

