See Further Detailed Guides Of The Login Process at www.techtricksworld.com
By clicking www.techtricksworld.com, users can detect more useful information for their login.
Visit site: www.techtricksworld.com
10 Best Sites Like CharaHub - TechTricksWorld
trend www.techtricksworld.com
238 People Used
What is My Login Keychain Password? - TechTricksWorld
tip www.techtricksworld.com
· “Change Password for Keychain Login Greyed Out” this term is being searched by many Mac users because they don’t actually know that the option will never turn on for default keychain. For this, you have to do these: Create a new login Keychain first which you can do by going File >> New Keychain;
258 People Used
What is My Login Keychain Password? - TechTricksWorld
tip www.techtricksworld.com
Password is a confidential thing, and you need to enter it while logging into any website you have previously signed up for. Remembering a lot of passwords is nearly impossible, thus people use password managers. However, when you use macOS, there is a default password manager, Keychain which stores and manages all the passwords on your Mac computer.
170 People Used
What is My Login Keychain Password? - TechTricksWorld
trend www.techtricksworld.com
Password is a confidential thing, and you need to enter it while logging into any website you have previously signed up for. Remembering a lot of passwords is nearly impossible, thus people use password managers. However, when you use macOS, there is a default password manager, Keychain which stores and manages all the passwords on your Mac computer.
134 People Used
What is My Login Keychain Password? - TechTricksWorld
new www.techtricksworld.com
Then click "Reset My Default Keychains" This will reset the default Keychains completely. Now, In the Finder on your Mac, choose Apple menu > Log Out. When you log in again, save your current login password in a keychain.
382 People Used
What is My Login Keychain Password? - TechTricksWorld
tip www.techtricksworld.com
Password is a confidential thing, and you need to enter it while logging into any website you have previously signed up for. Remembering a lot of passwords is nearly impossible, thus people use password managers. However, when you use macOS, there is a default password manager, Keychain which stores and manages all the passwords on your Mac computer.
85 People Used
What is My Login Keychain Password? - TechTricksWorld
new www.techtricksworld.com
Keychain is the password management app on macOS, and this comes preinstalled. It stores all the passwords such as system passwords, website passwords, and all. When you log in somewhere, it asks you if you want to remember the passwords.
352 People Used
What is My Login Keychain Password? - TechTricksWorld
best www.techtricksworld.com
Keychain is the password management app on macOS, and this comes preinstalled. It stores all the passwords such as system passwords, website passwords, and all. When you log in somewhere, it asks you if you want to remember the passwords.
354 People Used
What is My Login Keychain Password? - TechTricksWorld
new www.techtricksworld.com
Once you have created a new Keychain, it will show here as I created one "atishranjan" Now, right-click on this one "atishranjan", and click "Make Keychain "atishranjan" Default. Now, Right-click the original login keychain and select " Change password for Keychain "login". You will see this is not greyed out anymore.
420 People Used
What is My Login Keychain Password? - TechTricksWorld
trend www.techtricksworld.com
Password is a confidential thing, and you need to enter it while logging into any website you have previously signed up for. Remembering a lot of passwords is nearly impossible, thus people use password managers. However, when you use macOS, there is a default password manager, Keychain which stores and manages all the passwords on your Mac computer.
217 People Used
What is My Login Keychain Password? - TechTricksWorld
best www.techtricksworld.com
Password is a confidential thing, and you need to enter it while logging into any website you have previously signed up for. Remembering a lot of passwords is nearly impossible, thus people use password managers. However, when you use macOS, there is a default password manager, Keychain which stores and manages all the passwords on your Mac computer.
308 People Used
What is My Login Keychain Password? - TechTricksWorld
top www.techtricksworld.com
Password is a confidential thing, and you need to enter it while logging into any website you have previously signed up for. Remembering a lot of passwords is nearly impossible, thus people use password managers. However, when you use macOS, there is a default password manager, Keychain which stores and manages all the passwords on your Mac computer.
194 People Used
How to Download Scribd Documents Without Download Option?
best www.techtricksworld.com
How to Download Document from Scribd? Well, the best option to download the documents from Scribd would be using the Download or Print option. However, if you do not have an account with Scribd and checking out how to download Scribd documents without download option, the following tips would be quite helpful.
159 People Used
How to create a sprint in JIRA? - TechTricksWorld
trend www.techtricksworld.com
Yes, if you want to create Sprint in JIRA, you need to have a Jira account and a good understanding of how JIRA works. If you do not have a Jira account, you can create one. If you are just trying to get a feel of how to work with Jira before actually opting for the tool, you can choose the free trial and check out the different options and ...
493 People Used
How to Delete Kik Messages on Both Ends?
trend www.techtricksworld.com
You cannot delete Kik Messages on both ends. That would mean you can only delete a Kik Message on your phone. If you want to delete it on another device, or the one that you have sent it to, you are in for a disappointment. You will need physical access to the receivers' phone and only then will be able to delete the message from the phone.
445 People Used
How to Create Fake Discord Messages? - TechTricksWorld
best www.techtricksworld.com
Compared to the Developer Tools option and the inspect elements section, the Embed Editor is an excellent option as a fake Discord message maker. It is an online tool and lets you create your own Discord fake messages. It has an easy to use interface and offers a preview field to witness the changes you have made.
216 People Used
What is My Login Keychain Password?
new www.techtricksworld.com
As said above, your login keychain password is the same as the password you use to login to your Mac. Moreover, for added security, you can update the keychain password to something else as well. Even you can change different settings of Keychain from the Edit Menu, as it should be locked for certain minutes of inactivity or lock when Mac is in ...
107 People Used
What is My Login Keychain Password? - TechTricksWorld
best www.techtricksworld.com
Password is a confidential thing, and you need to enter it while logging into any website you have previously signed up for. Remembering a lot of passwords is nearly impossible, thus people use password managers. However, when you use macOS, there is a default password manager, Keychain which stores and manages all the passwords on your Mac computer.
238 People Used
How to Find Passwords on Mac Keychain? - TechTricksWorld
top www.techtricksworld.com
Password is a confidential thing, and you need to enter it while logging into any website you have previously signed up for. Remembering a lot of passwords is nearly impossible, thus people use password managers. However, when you use macOS, there is a default password manager, Keychain which stores and manages all the passwords on your Mac computer.
186 People Used
What is My Login Keychain Password? - TechTricksWorld
great www.techtricksworld.com
What is Keychain? Keychain is the password management app on macOS, and this comes preinstalled. It stores all the passwords such as system passwords, website passwords, and all. When you log in somewhere, it asks you if you want to remember the passwords.
96 People Used
Popular Searching
Saving Tips
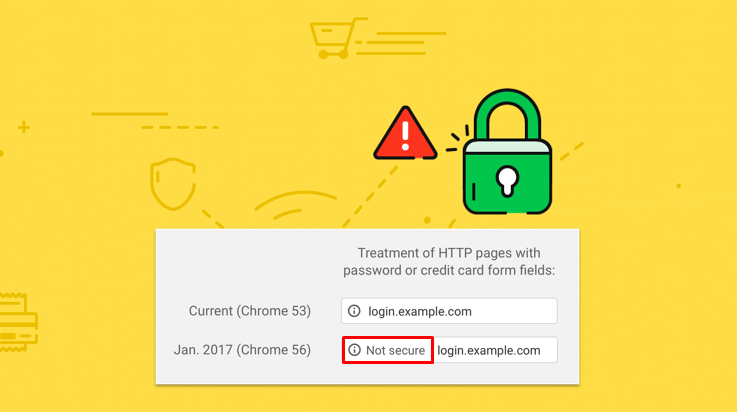
Things to Know When Entering Your Account to "Not Secure" Website

Face ID VS Fingerprint: Which Is More Secure?

Tips to Getting Your Account Credentials Back Easily

