Www.wellcarepdp.com Login
Top Results For Www.wellcarepdp.com Login
WellCare Health Plans, Inc : Login
best member.wellcare.com
© 2019 Wellcare. All Rights Reserved. Privacy Policy More ›PDP | WellCare
new www.wellcare.com
· Medicare Prescription Drug Plans are also known as Medicare Part D. Select your state to find information about your WellCare plan. More ›Trending Searches
WellCare CustomPoint - 2021 Materials Ordering Now ...
trend www.nandfinc.com
· CustomPoint – 2021 Materials Ordering Available WellCare is excited to announce 2021 sales materials ordering is now available in CustomPoint! Many improvements have been made to CustomPoint, the broker materials ordering portal. 2021 Sales materials for all Centene health plans are available to order in CustomPoint: Allwell, Ascension Complete, Fidelis Care, Health Net, & WellCare ... More ›WellCare Health Plans, Inc : Login
best member.wellcare.com
You have successfully logged out. Member Sign-In. User ID More ›WellCare Health Plans, Inc : Login
best portal.wellcare.com
The all-new provider portal is available. If you don’t yet have an account for the new portal, all you have to do is login with your existing username and password review your information, enter a phone number and select three new security questions. You will then need to request affiliation to your WellCare contract(s) in order to get access to the new portal. More ›Login - Customer Portal - Eatel Business
@2018 EATEL All rights reserved. All logos, trademarks and copyrights are properties of their respective owners. More ›WellCare of Georgia, Inc : Login
If you are a Medicare or PDP member, please log in here.. Member Sign-In * Username Username * Password More ›New Jersey Medicaid Plan : Login
If you are a Medicare or PDP member, please log in here.. Member Sign-In * Username Username * Password More ›WellCare Health Plans, Inc : Login : Producer Site Not ...
trend portal.wellcare.com
This site is no longer active. Please access our new enrollment system, Ascend, to submit your telephonic enrollment using the following link: More ›WellCare Plans
trend www.wellcareplans.com
Privacy Policy. ©2020 WellCare. All Rights Reserved. More ›PDP Gaming Official Site - Audio, Controllers, Power ...
great wellcare.pdp.com
PDP is a top video game accessory company that creates high performance designed products to enhance the gaming experience. More ›WellCare Health Plans, Inc : Member
Are you a new member? You can register on the member portal on or after your plan’s effective start date. If you have trouble registering on the portal, please reach out to customer service. More ›Pharmacy | WellCare
Pharmacy. WellCare is committed to working with providers to improve members' health and well-being. The following information will help your patients get the most out of their pharmacy benefits. More ›WellCare
Health Insurance CompanyPopular Searching
Useful Blogs

What Is Data Breach? How Can User Detect a Data Breach to Report?

How Can I View Private Instagram Profiles?
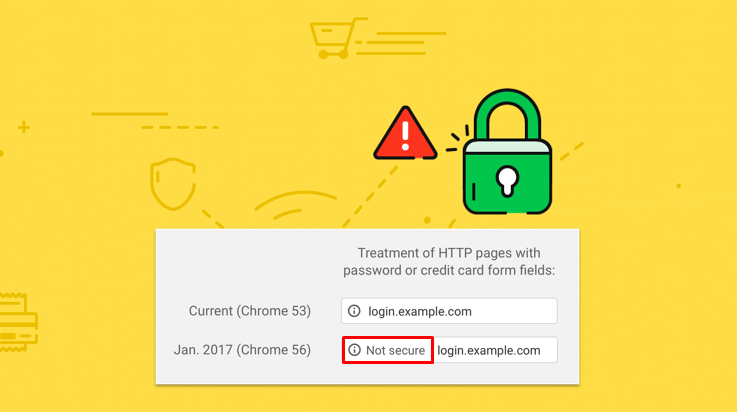
Things to Know When Entering Your Account to "Not Secure" Website

Find out If Someone Else is Logging in Your Facebook Account
We found a lot of relevant information for Www.wellcarepdp.com Login. We provide the official link and a number of helpful pages for the login above. They are reliable sites collected by LoginNote. Please check it thoroughly!
How do you collect the data for Www.wellcarepdp.com Login?
We prioritize finding the official login links for all searches. Besides that, relevant information such login instructions, requirements, and accounts may be also given.
I have an experience about Www.wellcarepdp.com Login, how can I send you?
That’s great. It is certain that your login experience is very valuable for other users. We will really appreciate if you can share it with us.
What information of Www.wellcarepdp.com Login will be provided besides the login link?
For each search from the user, besides the login link, we also provide relevant information such as register guiding, requirements, and accounts. It is similar to the search 'Www.wellcarepdp.com Login'.
Where can I find the official link for Www.wellcarepdp.com Login?
At each result for searches, we also enclose a link heading to the official login portal. It is often on the top of the recommendation page. The official link for Www.wellcarepdp.com Login is the same.





