See Further Detailed Guides Of The Login Process at geojones.org
By clicking geojones.org, users can detect more useful information for their login.
Visit site: geojones.org
Rebekah Jones - Geographer & Environmental Enthusiast
trend geojones.org
In April 2020, my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida Department of Health, received praise from White House Advisor Dr. Debora Birx, logged more than 100 million views within six weeks, and was hailed as the national gold-standard for data transparency ...
330 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
best geojones.org
In April 2020, my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida Department of Health, received praise from White House Advisor Dr. Debora Birx, logged more than 100 million views within six weeks, and was hailed as the national gold-standard for data transparency ...Meet Rebekah‧Portfolio‧News and Posts‧Education‧Research and Publications‧Graphic Design
131 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
trend geojones.org
Rebekah Jones Geographer & Environmental Enthusiast. ... In April 2020, my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida Department of Health, ... Your new dashboard for COVID19 is impressive, and it inspires me to refresh some of my data analytics skills from ...
216 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
great geojones.org
Rebekah Jones Geographer & Environmental Enthusiast. ... In April 2020, my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida Department of Health, received praise from White House Advisor Dr. Debora Birx, ...
212 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
tip geojones.org
Rebekah Jones Geographer & Environmental Enthusiast ... my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida ... I founded Florida COVID Action to track and analyze all authoritative data about the COVID-19 pandemic in Florida when state leadership refused to do so ...Meet Rebekah‧Portfolio‧News and Posts‧Education‧Research and Publications‧Graphic Design
243 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
great geojones.org
In April 2020, my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida Department of Health, received praise from White House Advisor Dr. Debora Birx, logged more than 100 million views within six weeks, and was hailed as the national gold-standard for data transparency ...
146 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
hot geojones.org
In April 2020, my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida Department of Health, received praise from White House Advisor Dr. Debora Birx, logged more than 100 million views within six weeks, and was hailed as the national gold-standard for data transparency ...
378 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
hot geojones.org
Rebekah Jones Geographer & Environmental Enthusiast. ... In April 2020, my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida Department of Health, received praise from White House Advisor Dr. Debora Birx, ...Meet Rebekah‧Portfolio‧News and Posts‧Education‧Research and Publications‧Graphic Design
280 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
best geojones.org
In April 2020, my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida Department of Health, received praise from White House Advisor Dr. Debora Birx, logged more than 100 million views within six weeks, and was hailed as the national gold-standard for data transparency ...
259 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
best geojones.org
In April 2020, my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida Department of Health, received praise from White House Advisor Dr. Debora Birx, logged more than 100 million views within six weeks, and was hailed as the national gold-standard for data transparency ...
371 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
top geojones.org
Rebekah Jones Geographer & Environmental Enthusiast. ... In April 2020, my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida Department of Health, received praise from White House Advisor Dr. Debora Birx, ...
422 People Used
Alumna Tracks the COVID-19 Outbreak, by ... - Rebekah Jones
new geojones.org
When the COVID-19 virus outbreak hit Florida and the public needed information, Rebekah Jones '12 was ready for action. As the geographic information systems (GIS) manager for the State of Florida Department of Health (DOH), she built the state's COVID-19 Data and Surveillance Dashboard, an interactive website that provides key information ...
306 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
great geojones.org
Rebekah Jones Geographer & Environmental Enthusiast. An Introduction. ... Enter your email address to follow this blog and receive notifications of new posts by email. Join 375,928 other followers Email Address: Follow . Contact Me. Bek@GeoJones.Org. Search my site ...
343 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
new geojones.org
In April 2020, my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida Department of Health, received praise from White House Advisor Dr. Debora Birx, logged more than 100 million views within six weeks, and was hailed as the national gold-standard for data transparency ...
435 People Used
Rebekah Jones - Geographer & Environmental Enthusiast
trend geojones.org
Rebekah Jones Geographer & Environmental Enthusiast. ... In April 2020, my COVID-19 Data and Surveillance Dashboard, which I built while working as Geospatial Information Sciences Manager at the Florida Department of Health, received praise from White House Advisor Dr. Debora Birx, ...Meet Rebekah‧Portfolio‧News and Posts‧Education‧Research and Publications‧Graphic Design
284 People Used
Popular Searching
Saving Tips

How to Log in to Amazon without Verification Code?
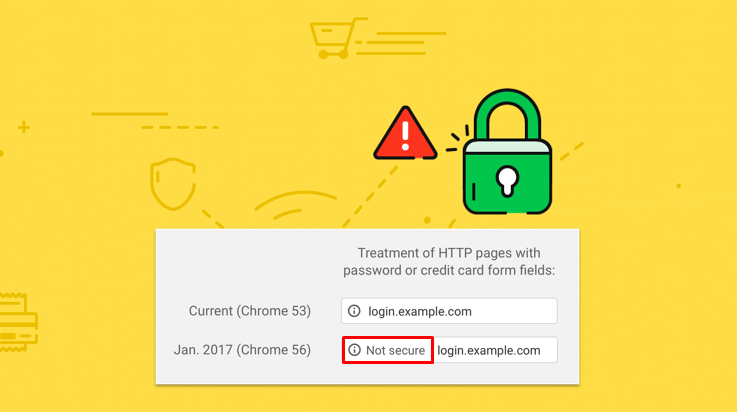
Things to Know When Entering Your Account to "Not Secure" Website

What Is Data Breach? How Can User Detect a Data Breach to Report?

